 _ "Sharing Your Vacation With Friends & Family In Real Time" Due to the growing number of free blog, photo-sharing, and social networking websites, such as Twitter, Facebook, Delicious, YouTube, and Where are You Now? (WAYN), loved ones do not have to wait to hear about your trip. Choosing a Social Network or Photo-sharing Site There are multiple websites that allow users to share photos or to publish a more in-depth blog, including the following: - Flickr
- Online photo management and sharing application
- You can control permissions - Picasa
- Software download that helps you organize, edit, and share your photos
- You can control permissions - Traveljournals.net
- Online travel journal, allows you to share pictures and stories - Facebook & Twitter
- Keep up with friends and upload photos
Once you choose the site you would like to use, you'll have to create a user account for that site before you can begin sharing your vacation. What Technology to Pack Before leaving for your adventure, be sure to bring the following items: - A digital camera or camera phone
- A computer (either your own laptop, or a computer located in a hotel, library, cyber café, cruise ship—the options are increasing, daily)
- A media card reader, if your laptop doesn't have one
- For travel outside of North America, a power adapter for recharging your mobile phone or laptop
 _"3 Ways to Improve Working on a Virtual Team"Working on a virtual team can be a challenge. Here are some suggestions to help with virtual team management and to help your team work more effectively. Use Instant Messaging for Unscheduled Meetings
Use instant messaging to get quick answers or opinions from your teammates. IM programs are free. At a glance, you can check your coworkers' status to see whether they're available to chat online. The following are different ways to use IM. - Use a webcam to connect visually. - Use multi-person chat to conduct a spontaneous online meeting. - IM your teammates' cell phones when they're away from their computers. - Use a Virtual Conference Room
Web-based conferencing, or web conferencing, makes it possible to brainstorm, create a slide presentation, have a staff meeting, or conduct training sessions with a group of people—even if they are thousands of miles apart.
The following is needed to begin:
Using either Lync or Live Meeting requires coordination with your IT department to create a subscription account or to install a server.
- Share Meeting Information
When organizing meetings, the simplest way to keep your team members on the same page is to create a web-based, shared calendar that everyone can edit. Then you'll know that everyone is looking at exactly the same schedule and can see any changes instantly. You can create a shared calendar in a variety of programs, including Windows Live Hotmail and Outlook.
The following is needed to begin:
In Windows 7, the calendar is part of Hotmail. Sign up for a free Hotmail account by getting a Windows Live ID.
 _As more people begin using laptops, the number of laptop thefts are increasing. If your laptop computer is stolen, or if someone gains access to your files, your company, personal and financial data can be exposed. See the following tips on how to stay protected.- Don't use computer bags.
Computer bags only make it more obvious that you're carrying a laptop. The use of padded briefcases or suitcases is recommended. - Use passwords that are strong, and not kept in the computer bag.
Strong passwords make it more difficult to break into your computer deterring individuals from trying to access your files. - Encrypt data.
With the Windows Operating System, you can choose to encrypt files and folders. Which causes individuals to not be able to read data and see your information. - Keep an eye on your laptop.
Don't lose sight of your bag, such as when going through airport security. - Buy a laptop security device.
If you need to leave your laptop in a room or at your desk, use a laptop security cable to securely attach it to a heavy chair, table, or desk. The cable makes it more difficult for someone to take your laptop. There are also programs and devices that will report the location of a stolen laptop. - Do not leave your laptop in a hotel room.
If you must leave your laptop in the hotel room, place the do not disturb sign on the door. - Put your name and contact info on the laptop.
In addition to putting your name on the laptop, it is also recommended that you include a, "Reward with no questions asked if returned." tag line as well. Both of these increase the chance of your laptop being returned, no matter what the circumstance.
 _When your RAM is unable to store all of your work easily, your computer slows down and becomes more difficult to run. One of the solutions is to expand the space—or install more RAM. Before purchasing anything, it is necessary to know how much memory is currently in your computer and what type of memory to buy. How to Find Out How Much RAM Your Computer Has There are two different ways to find out how much RAM your computer has including the following: - You can open the System Information dialog box to see the installed physical memory
- You can go to Control Panel
To open System Information perform the following steps: - click Start, click All Programs
- click Accessories
- click System Tools
- click System Information
- In the left pane, select System Summary. The Installed Physical Memory (RAM) entry in the list tells you how much RAM your computer has.
_The Installed Physical Memory (RAM) entry in the System Information list tells you how much RAM your computer has.
How to Find Out How Much RAM is Needed
The operating system determines the amount of RAM that's needed. Systems running Windows 7, Windows Vista, or Windows XP, should have the minimum recommended amount, however more may be better. If the PC is solely used for surfing the Internet and writing letters, it may only require the minimum amount of RAM required to run the version of Windows you have installed on your computer. In order to allow for the best performance possible —consider increasing the RAM on your computer to at least 2 gigabytes (GB). 4 GB is ideal.
How to Figure Out What Type of RAM is Needed
Contact the manufacturer or use an online memory advisor, such as those from Crucial Technology or Kingston Technology. These memory advisors use information that you enter about your computer model and do a memory check for your specific PC that tells you which products work with your system.
Installing the New RAM
It is recommended that you consult a professional if you have not installed RAM before. We offer affordable installation services and can assist you with increasing your RAM. Call our office for more details and to setup an appointment.
 _Learning better file management can improve time management skills and increase productivity at work. The following tips are just a few ideas to improve file management skills. Ideas for Managing Your Files and Folders - Use a Consistent File and Folder Naming System. It is imperative that you develop a naming system for the kinds of files you create most often and then continue to use that system - allowing for more organized, easier to navigate folders.
- Keep File and Folder Names Short. Do not use long names for folders or files, as this can cause a cluttered look, which may make it more difficult to find a particular file.
- Separate Ongoing and Completed Work. To keep the Documents folder from becoming too cluttered, use it for only active files, which will allow easier access to the active items. Completed files should be moved to a different folder or location, such as the following:
- Desktop folder
- Special archive folder
- Flash drive
- External hard drive
- CD
- Similar Items Should be Stored Together. Restricting folders to a single document type makes it easier for you to find files. For example, putting all of your graphics in a single folder allows for easy access to the slide show feature in Windows Explorer.
- Storing Documents Online. Microsoft SharePoint 2010, Windows Live SkyDrive, and DropBox allow you to save documents safely online. As a result, it is easy to access them from outside the office, share them, and edit them online by using Office Web Apps.
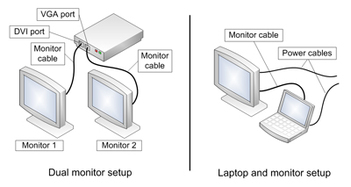 _It often times becomes necessary to have more computer monitor space. One way to increase your amount of screen space is to buy an inexpensive second monitor or make use of an old monitor and connect it to your computer (if you're using Windows 7, Windows Vista, or Windows XP)—allowing for more free screen space in which you can work. Dual Monitor Setup Checklist- Two or more monitors (one, if you’re setting up a laptop), which may be of any combination including the following: flat-panel LCD monitors, CRT monitors, one of each, or even a TV screen as a monitor. If you are going to buy a monitor consider the following:
- Picture quality
- Screen size
- Screen resolution
- Compatibility with your computer port
- Higher contrast ratio
- Color richness
- Two monitor cables that match the connection types of your computer to connect the monitors to the computer (one for a laptop).
- A monitor connection on your computer for each monitor you want to connect such as the following:
- Digital Visual Interface (DVI) connectors
- Video Graphics Array (VGA) connectors
- HDMI (High Definition Multimedia Interface) connectors
- S-Video connectors for using your TV as a monitor
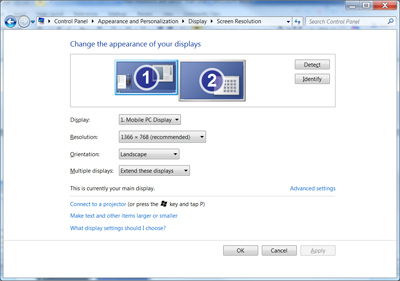
_Connecting of Monitor Cables Make sure the monitor is plugged in and turned on. Your computer should automatically detect the second monitor. If you’re using Windows XP, you’ll need to enable Dualview. When your computer detects the monitor, it should also automatically detect and apply the display settings appropriate for the monitor. Configure your displays If necessary, you can drag the monitor icons so that they are arranged in the same way as the monitors on your desk. Click Identify to verify which monitor is 1 and which monitor is 2. You’ll see the numbers appear on your monitors. Under Multiple displays, you can also adjust what you see on the second monitor. You have the following choices: - Extend your displays. This spreads your desktop over both monitors and lets you drag items between the two screens. After your monitor is set up, you can use your mouse to grab the title bar (the top portion) of a window and drag it to your new display.
- Duplicate your displays. This displays the same desktop on both monitors. For a laptop, this is the default setting. This is useful if you're giving a presentation with your laptop connected to a projector or large monitor.
- Show your desktop on only one monitor. This is most commonly used with a laptop if you want to keep your laptop screen blank after you connect to a large desktop monitor.
When you disconnect the additional monitor the following occurs: - Original display settings are restored to your primary display
- All open files and program windows are moved to the primary display
The next time that you connect the same monitor, the Windows operating system automatically applies the display settings that you used the last time that you connected this monitor. Want more tips like these? Subscribe, it's free!
Avoid Being Hacked Hacking is a major issue, and hackers use many tricks in an attempt to access your data. There are steps you can take to protect yourself and your data from the most common hacking methods. Anti-virus software (Norton, McAfee, Sophos, etc.)SPAM- Most spam will not cause harm, however the best practice is to delete emails from unknown sources and those with attachments. If you reply or attempt to unsubscribe, this will confirm to the spammer that your account is active and in use.
Anti-spyware- "Malware" or "spyware" are terms used to describe malicious software that can be used to cause denial of service attacks or harvest sensitive data (credit card numbers, etc.) from your computer. These programs can cause you to receive pop-up ads and/or track your web surfing habits. Attachments can be harmful to your computer and can carry malicious viruses and malware. There are tools available, such as Spybot Search and Destroy or Ad-Aware, that scan your computer and identify malware and other harmful items. Once found, these programs give you the option to delete the items. These programs also need to be updated so that you have the most current versions.
Patches, security updates, etc.- Virus writers and hackers will exploit holes in programs to gain access to your computer. To keep your computer up to date with the latest security fixes and patches, visit http://update.microsoft.com/microsoftupdate on a routine basis. If are you running an Apple or Linux machine, be sure to check routinely for updates also.
Downloading Content
Knowing how to use your computer responsibly is important to protect both yourself and those arround you. P2P or peer-to-peer programs have made news recently across the nation. Suits are being filed against users regarding illegal activity such as improper music downloads. We strongly suggests that you do not use peer-to-peer programs.
Always respect copyright laws. This includes printed and digital material. Do not engage in illicit music, video, or movie downloads. Please be aware that the infringement of copyrighted music, videos, or movies can be punished by up to five years in prison and $250,000 in fines. Repeat offenders can be imprisoned up to ten years. Individuals also may be held civilly liable, regardless of whether the activity is for profit, for actual damages or lost profits, or for statutory damages up to $150,000 per infringed copyright.
Also, please be advised that all telecoms and internet providers will notify the appropriate authorities whenever requests are made by the Recording Industry Association of America or any other legitimate enforcement or monitoring entity.
Social Networking (Facebook, MySpace, etc.) Social networking through the use of such services as Facebook have become part of everyday life for many of us. These types of networks can be used to find others with common interests, share personal information, and communicate with friends. While cyber communities can be used in positive ways, it is important to use common sense and keep several key thoughts in mind: - The information you place online can influence your future. Pictures that may demonstrate behaviors that are questionable or suggestive can be viewed by anyone on the Internet, including possible future employers. There have been instances where graduates have had their Facebook page called up during the interview process.
- Making your information private does not mean that others are unable to view the material. Hackers have many tricks that enable them to view what is thought by you to be off limits. You should also remember that pictures or other information posted for a short period of time and then removed by you may have been downloaded by others and exist in cyberspace for years to come.
- Be safe. Use common sense when entering information on Web sites. There is the illusion that your information is there for only your friends to view but realize that your information can be passed on to others that may not have your well being in mind. It is strongly suggested that you do not post information such as phone numbers or your place of residence.
- Think about how you represent yourself and others. It is not only important to take note of what you say about yourself online but equally important are the comments you make about others. You do not want to face alleged violations that claim inappropriate behavior on your part.
 The most basic step you can take to prevent power loss on your mobile PC is to invest in a high quality battery and always keep a spare on hand. Splurging on a quality battery and spare can save you from hours of lost access to your mobile PC. Battery Care Once you've invested in a good battery, you need to take care of it. To clean your battery contacts, first turn off and unplug your mobile PC. Remove the battery and wipe its metal contacts and its contacts inside the device with a cotton swab dipped in rubbing alcohol. Let dry completely before reinstalling and reconnecting to a power source. Repeat every two to three months. Modern lithium ion batteries can be recharged and partially discharged time and time again, but you should never fully discharge them. Nickel-metal hydride (NiMH) batteries common to older laptops should be completely drained and recharged every one to three months. After mastering the basics of battery care, make sure you are utilizing your mobile PC's built in energy saving features. Optimize Your Power Settings The hard disk and display on your mobile PC consume the most battery power. Choose a power plan, referred to as a power scheme in Windows XP, to reduce the use of power-hungry functions and lessen screen brightness. Utilize the following battery-saving states: - Sleep or Standby
In a sleep state, your hard disk and display turn off, and all open programs and files are saved in Random Access Memory. In case of a crash or power loss, save your work before placing your system in sleep mode. Your mobile PC should wake up quickly from sleep, and your desktop and files should appear just as you left them.
- Hibernation
When your computer hibernates, it saves everything to its hard disk before shutting down. When you restart, your desktop should be restored exactly as you left it. Hibernation takes a bit longer to wake up from than sleep, but it uses less power.
Further Tips for Lowering Your Energy Use: - Turn off your wireless device when you're not connected to a wireless network but you're using your mobile PC.
- Turn off scheduled tasks.
- Keep the use of tools in the notification bar minimal.
- Limit power-intensive activities such as gaming, watching a DVD or listening to a CD.
- Reduce power consumption by adding memory (RAM) to your mobile PC.
|









 RSS Feed
RSS Feed